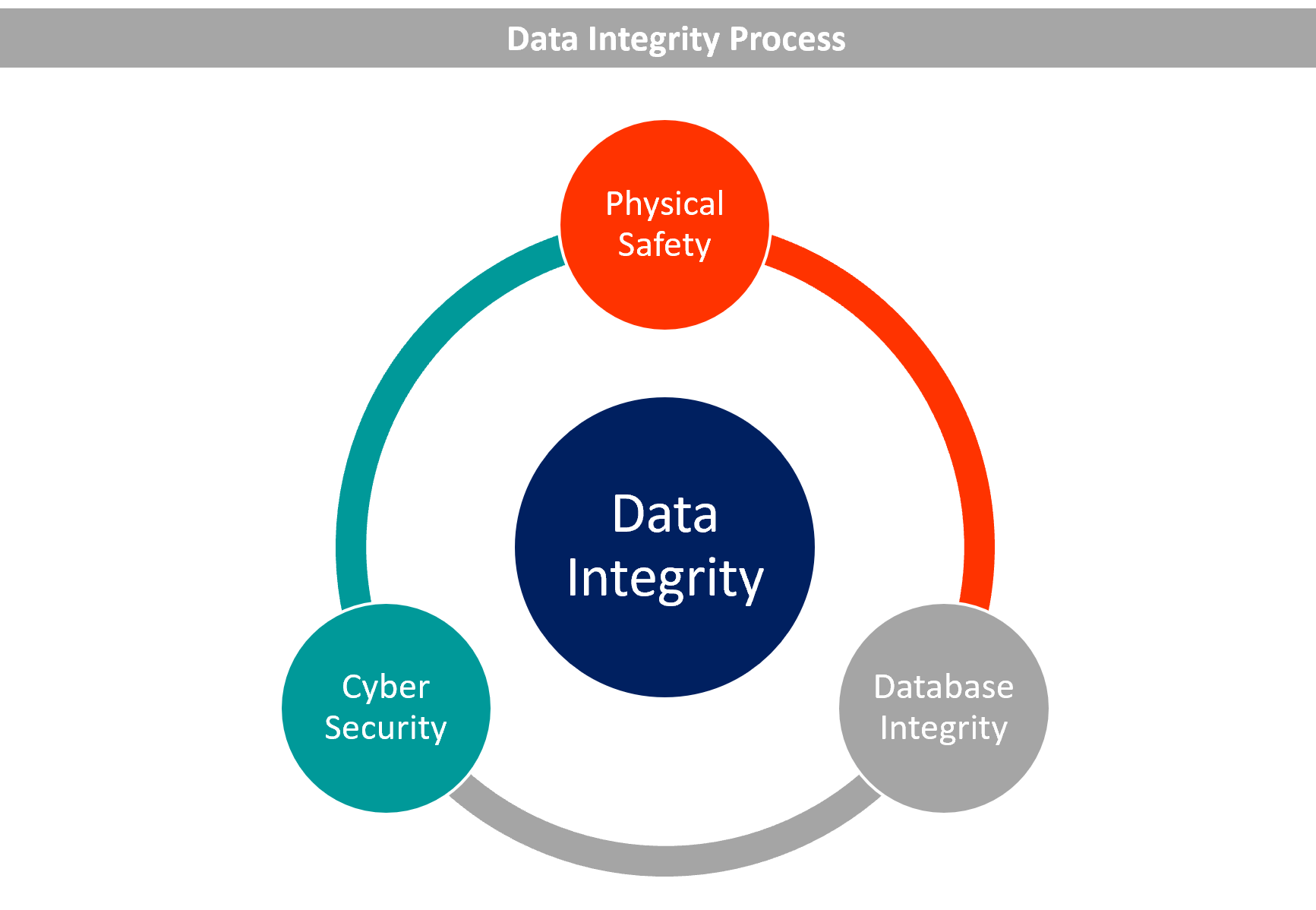
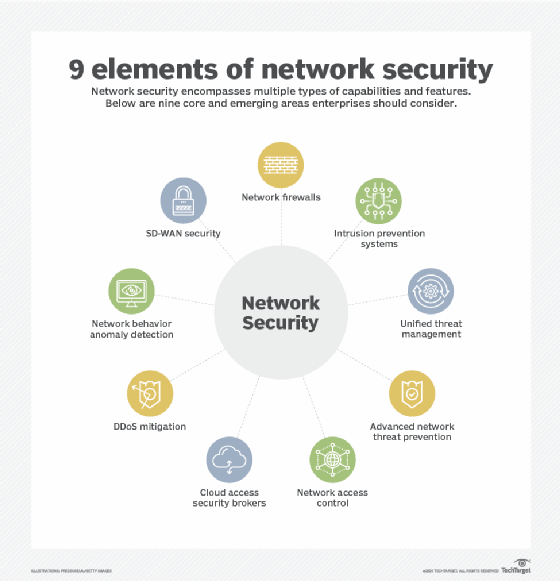
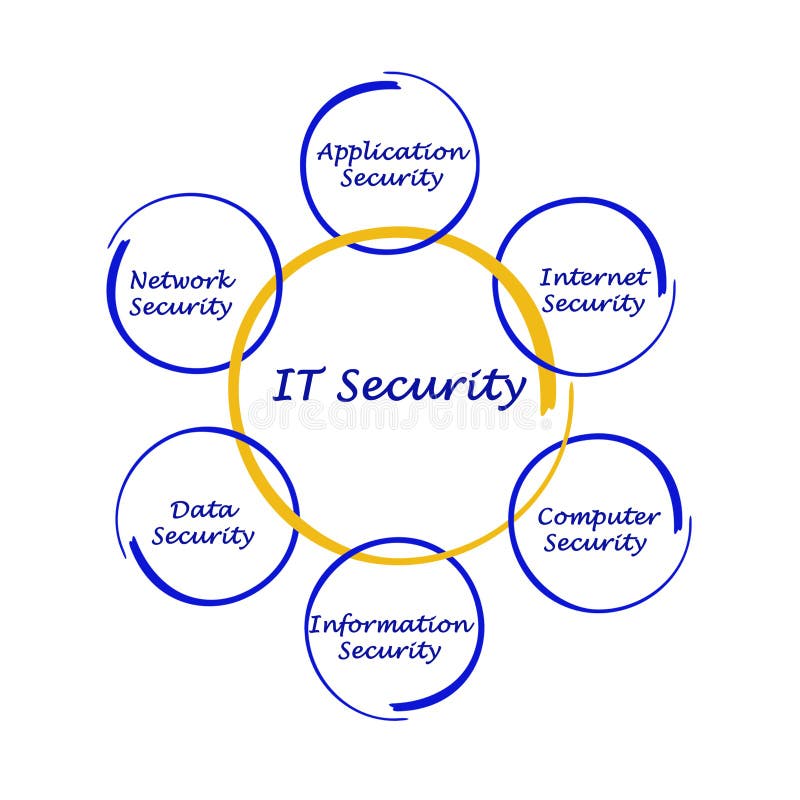
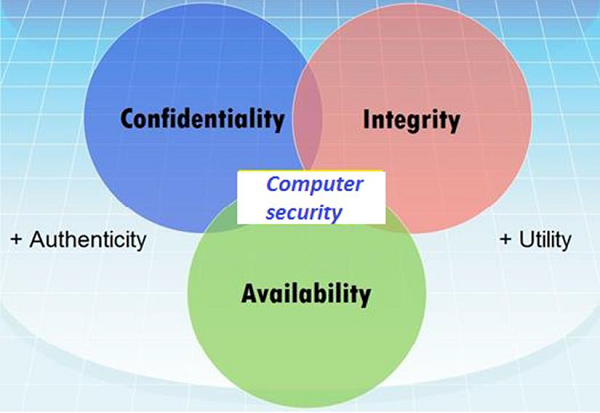
Components of Computer Security, Threats - Slides | ECS 235A | Study notes Computer Science | Docsity

Chapter 1: Introduction Components of computer security Threats Policies and mechanisms The role of trust Assurance Operational Issues Human Issues Computer. - ppt download

م. إبراهيم الرميان on Twitter: "2⃣Infographics on Information and Communications Technology Security https://t.co/g7JOFdBjiD https://t.co/2EELmmwyo4" / Twitter